New Android vulnerabilities could expose nearly all devices to hacks
"Stagefright" issues found within code are deemed "worst discovered to date," but Google is aware

Many of us view MMS messages throughout each and every week, but if you have an Android phone and the message comes from a malicious source, it could well make your device vulnerable to hackers.
That’s according to Zimperium Mobile Security, whose researchers discovered a host of vulnerabilities within Stagefright, the media playback engine found within Android 2.2 and higher. Google surely now regrets that name, given the problems that Stagefright could introduce.
Zimperium says that the malicious code can be executed simply by receiving the MMS message, so anyone with your phone number could send it – and there’s no indication that anything has changed (as seen in Zimperium’s example flow below). You don’t even need to open the MMS: the preview notification alone does the trick, which makes this exploit much more devious than most.
It may even be possible for someone to send a message and then delete it remotely without you even seeing it. Once the trojan horse is on your phone or tablet, the sender could have remote access to your device and files, and could use that access to steal data or destroy the phone’s contents. The problem could theoretically affect upwards of 95% of Android devices, or about 950 million of them worldwide.
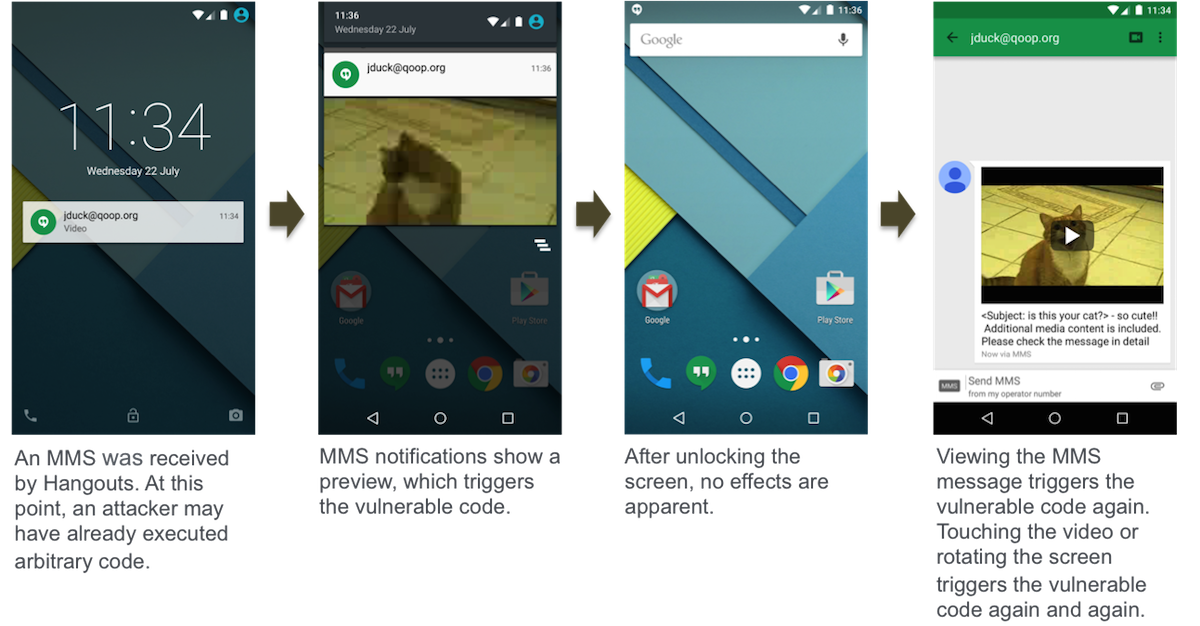
Yes, it all sounds quite terrible, but we’re not trying to spook Android owners – and neither is Zimperium. Like a responsible firm should, the company reported the issues to Google in April, and Google implemented patches for manufacturers and carriers to release. That means that some phones may already be secured – like the Blackphone.
But many Android partners haven’t yet issued those patches to consumers – alas, the typically slow Android update cycle – which means there’s plenty of uncertainty over which phones are vulnerable and how you can avoid potential issues. The news is fresh, so we won’t have a lot of those answers just yet; stay tuned, however, and we’ll share anything more we hear about updates and potential recovery options if you’re affected.
[Source: Zimperium Labs via Wired UK]



